Top 10 Best Search Engines Used By Hacker|Shadow Cyber Security
We all use the internet search engine in our daily life whether to search for a recipe or to complete an assignment or some other task, but have you ever wondered what kind of tools and internet search engines hackers might be using to find out the vulnerabilities of various systems through the internet.
Here we have brought the best 10 out of all the hacker search engines available:-
1. Shadon
In contrast to google, which is searching the web for simple websites, Shadon is also a search engine, but one specifically designed for IoT devices. It ranks the unseen pieces of the internet that most users would never see.
Sahdon is considered one of the most dangerous search engine. Although is not easy to use for most internet users, experts in cyber security and hackers can work with it.
2. Greynoise
Greynoise allows you to identify servers and users that are scanning various networks and devices fro vulnerabilities using search engine like shadon or even more advanced and malicious ones.It is very useful for hackers and security personnel that deal with thousands of IP addresses to filter out unwanted internet background noise that interfaces with hacking or security operations.
3. Censys
This is a service similar to shadon as it also monitors devices that are connected and exposed on the internet and collects this data and provide them in the form of a search engine where a user can find the reports and data how the various websites, certificates and devices are deployed and configured.
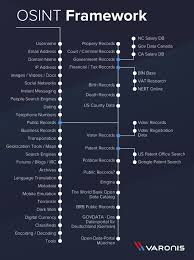
4. OSINT Framework
OSINT Framework stands for Open Source Intelligence Framework and it gathers information that is available from public sources and can be used for assessment. It is an essential cyber security framework and is mostly used in law enforcement, national security and other intelligence service. It includes email public records, usernames,email addresses, IP addresses and many more options to to choose from.
5. HIBP
HIBP stands for "Have i been pwned" is an internet search engine that is useful both for hackers and normal users because it finds out whether a particular email account has been compromised due to some data breach in the system information had been utilized in some way.If the particular account has been compromised, it can provide each detail of the breach and the type of information involved in that data breach.
6. PublicWWW
This is a search engine to find source code in the from of HTML, JavaScript, CSS, ets, available on any webpage. Testing this search engine, we can search for websites based on the their source code.Webpage that have used the similar code snippet thus allowing you to check for alphanumeric extracts, signatures and keywords that have been used in a particular webpage.
7.PIPL
This is a useful internet search engine for finding information about individual person using the phone number and email addresses and identifying them.It can reveal everything about a person, including their name, contact, professional, personal information, etc.
8. Hunter
This is the most used and dynamic internet search engine used by hackers for email address detection.Hunter search engine can be used to fine and retrive all the email addresses that are associated with a certain domain or organization. The displays a list of verified email addresses that come under domain including their activity, and the public resources that were used those addresses.
9. Zoomeye
This is a hacker friendly tool that acts as a navigation chart for finding and navigating our way towards vulnerabilities and threats in networks and system.It can be even represent the statistics of all the devices that are exposed through the internet from different browsers, servers,and countries etc.
10. WiGLE
This is an internet search engine to find wireless networks through coordination and is used for wireless network mappling.It can be used to identity and monitor insecure systems that are vulnerabilities to attacks or just for finding open networks in a particular area.
Shadow Cyber Security
Our Service is :-
1. web-application-penetration testing
2. network penetration testing
3. mobile app penetration testing
4. latest security patches
5. customer cyber solutions
6. iot penetration testing
7. cloud testing security
8. system penetration testing
9. malware family threads protraction
10. social media security provide
11. social engineering security
12. website/app design and development
These Time Cyber Attack Increase Every Year All Company Regular Basis For Any Cyber Security Advise Ya Question Plz Contact
phone no - 8700320447
website- http://shadowcybersecurity.com/
-----Thanks For Watching-----








Post a Comment
Post a Comment