Top Ransomware Attack In History | Shadow Cyber Security
"What is Ransomware attack?"
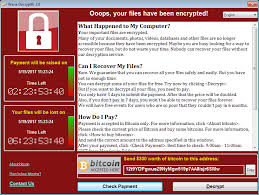
This is a type of malicious software that threatens to publish or blocks access to data or a computer system, usually by encrypting it until the victim pays a ransom fee to the attacker. In other many cases the ransom demand comes with a deadlines.
"Examples of Ransomware attack?"
Cerber is an example of evolving ransomware threats. It is distributed a s Ransomware as a service, Where cyber criminals can use it in exchange for 40% of profits. This is using an elaborate phishing campaign to infect anyone outside of post soviet countries.
Check out top Ransomware attack in history:-
1. AIDS Trojan or PC Cyborg 1989
This also known as PC Cyborg is the first registered ransomware in history. That is why its creator, Harvard trained biologist, Joseph Popp, can be considered the father of ransomware.They were sent to participants at the world health organisational AIDS conference, in Stockholm, Sweden in 1989.
This type of ransomware asked to victim send USD 189 to a mailbox in Panama. Only then could the data be recovered. But since it had weak encryption, there were no major problems.
2.I Love You Virus, 2000
This virus report date is May 10, this is both virus and worm. Worms propagate themselves through networks viruses destroy files and replicate themselves resulting from this particular hybrid, which includes overwhelmed email systems and lost files in limited to users of the Microsoft Windows operating system.
This is typically comes in the form of an email message from someone the recipient knows with an attachment called LOVE LETTER FOR YOU.TXT.VBS. The attachment is a Visual Basic Script VBS file.2 As long as recipients do not run the attached file, their systems will not be detected and they need only to delete the email and its attachment.
3.Code red computer virus, 2001
Code red was a computer worm observed on the internet on july 15, 2001. It attacked computers running Microsoft's IIS web server. This was first discovered and researched by eEye digital security employees Marc exploited a vulnerability discovered by Riley Hassell.
This is a worm that caused possible billions of dollars of damage in the summer of 2001. It contains the text string"Hacked by Chinese", which is displayed on web pages that the worm defences. It is also one of the few worms able to run entirely in memory, leaving no files on the hard drive or any other permanent storage.
4.Slammer, 2003
This computer virus randomly selected IP addresses, exploiting vulnerabilities and sending itself on to other machines. It used these victim machines to launch a DDos attack on several internet hosts, significantly slowing internet traffic.
The slammer computer virus worm hit banks in the U.S. and Canada especially hard, taking ATMs offline in many locations. Customers of Toronto's imperial Bank of commerce found themselves unable to access funds. The attack reared its ugly head again in 2016, launching from IP addresses in Ukraine, Mexico and China.
5. Mydoom computer virus, 2004
Mydoom is a very effective worm made to create zombies out of hundreds of thousands of computers. Hackers could then use each hijacked terminal to wage a denial of service attack toward a company they identified.
People all around the globe started mysterious email messages that said, "I" m just doing my job, nothing personal, sorry. Each email came with an attachment, and every time people checked their inboxes , they got another copy. The Mydoom virus was responsible.
Virus took over host computers, and most cleanup reporting focused on what people needed to do to eliminate the code. But two companies were the real victims.
6. CryptoLocker, 2013
The CryptoLocker ransomware has been added to our list because it was a milestone for its time, it was launched in 2013, CryptoLocker used a large, non standard encryption key, which was has challenged cyber security experts.
This is causes of losses of more than USD 3 million, infecting more than 200 thousand Windows based computers. CryptoLocker was distributions email using malicious files.
7. TeslaCrypt, 2015
This is several versions but the attacks of this one become famous because in the beginning, it infected game files, blocking maps and user profiles. The victim was forced to pay at least USD 250 to release the files. In this cases the hijacker required USD 500 per machine.
8. Petya, 2016
This i a ransomware that started to be propagated in 2016, via emails with malicious attachments, it's estimated that difference variations of Petya have caused more than USD 10 billion in financial losses.
This is affected different organisations in the world, such as companies and banks in the areas of trans portion, food, and health. Example the National Bank of Ukraine, Melendez, Merck and Rosanne.
9. WannaCry, 2017
Most devastating ramsomware attacks in history in terms of loss volume was caused by WannCry, launched in 2017. Estimated value at the time was USD 4 billion in losses. The release amount each machine was around USD 300.
This spread via email scams or phishing. Under worldwide, more than 200 thousand people and companies were affected, Example are FedEx, Telefornica , Renault. Today there are phishing emails calming that you were infected by WannaCry, demanding ransom payment.
10. Ryuk, 2019 and 2020
Most infections caused by ransomware, Ryuk is spread mainly vis malicious emails or phishing emails, containing dangerous links. Amount to be paid to release an entire system can exceed USD 300,000, making Ryunk one of the most expensive ransomware in history in average.
In this attacks already caused more than USD 60 millon in damage worldwide since this type or ransomware gained prominence in 2018 after stopping the operations of major newspaper in the United States.
"What is the most famous ransomware?"
CryptoLocker was one of the most profitable ransomware strains of its time, September to December 2013, CryptoLocker infected more than 2,50,000 systems.
"What happens if you pay ransomware?"
The FBI does not support paying a ransom in response to a ransomware attack. Paying a ransom doesn't guarantee you or your organisation will get any data back. It also encourages perpetrators to target more victims. the offers an incentive for others to get involves in this type of unauthorised activity.
"How do ransomware attacks start?"
This is often spread through phishing emails that contain malicious attachments or through drive by downloading. Drive by downloading occurs when a user unknowingly visits an infected web sites, then malware is downloading and installed without the knowledge.
"How are ransomware attacks resolved?"
Use anti virus or other security policies to block known payloads from launching. Make frequent, comprehensive backups of all important files and isolate them.
"Biggest ransomware attack in history?"
CryptoLocker debuted in September 2013, announcing a new era of ransomware attacks. It's believed this piece of malicious code was used to extort more than $3 million from its victims.
"What was the first big ransomware attacks?"
The first documented and purported example of ransomware was the 1989 AIDS Trojan also known as PS cyborg.
I hope you enjoy reading my blog? You can give any idea from your side and on which topic you can tell to write the next blog, thank you sincerely for reading our blog. Associated :-
Shadow Cyber Security
our service is :-
1. web-application-penetration testing
2. network penetration testing
3. mobile app penetration testing
4. latest security patches
5. customer cyber solutions
6. iot penetration testing
7. cloud testing security
8. system penetration testing
9. malware family threads protraction
10. social media security provide
11. social engineering security
12. website/app design and development
these time cyber attack increase every year all company regular basis
for any cyber security advise ya question plz contact
phone no 8700320447
website- http://shadowcybersecurity.com/
-----------Thanks for watching--------------










Post a Comment
Post a Comment